-
Other audit services
We help clients with the application and use of foreign financial aid of EU and other funds and help prepare financial reports.
-
Audit calculator
The calculator will answer if the company's sales revenue, assets or number of employees exceed the limit of an inspection or audit.
-
Payroll and related services
We perform payroll accounting for companies whether they employ a few or hundreds of employees.
-
Tax accounting
Grant Thornton Baltic's experienced tax specialists support accountants and offer reasonable and practical solutions.
-
Reporting
We prepare annual reports in a timely manner. We help to prepare management reports and various mandatory reports.
-
Consolidation of financial statements
Our experienced accountants and advisors help you prepare consolidation tables and make the consolidation process more efficient.
-
Consultancy and temporary staff
Our experienced specialists advise on more complex accounting transactions, rectify poor historic accounting, and offer the temporary replacement of an accountant.
-
Outsourced CFO service
Our CFO service is suitable for companies of all sizes and in all industries. We offer services to our clients in the required amount and competences.
-
Assessment of accounting processes
We help companies to implement accounting practices that are in compliance with local and international standards.
-
Accounting services for small businesses
We offer affordable service for small businesses. We help organize processes as smartly and cost-effectively as possible.
-
Cryptocurrency accounting
We keep up with blockchain technology to serve and advise crypto companies. We are supported by a network of colleagues in 130 countries.
-
Trainings and seminars
Our accountants have experience in all matters related to accounting and reporting. We offer our clients professional training according to their needs.

-
Business advisory
We offer legal support to both start-ups and expanding companies, making sure that all legal steps are well thought out in detail.
-
Fintech advisory
Our specialists advise payment institutions, virtual currency service providers and financial institutions.
-
Corporate advisory
We advise on legal, tax and financial matters necessary for better management of the company's legal or organizational structure.
-
Transaction advisory
We provide advice in all aspects of the transaction process.
-
Legal due diligence
We thoroughly analyze the internal documents, legal relations, and business compliance of the company to be merged or acquired.
-
In-house lawyer service
The service is intended for entrepreneurs who are looking for a reliable partner to solve the company's day-to-day legal issues.
-
The contact person service
We offer a contact person service to Estonian companies with a board located abroad.
-
Training
We organize both public trainings and tailor made trainings ordered by clients on current legal and tax issues.

-
Business model or strategy renewal
In order to be successful, every company, regardless of the size of the organization, must have a clear strategy, ie know where the whole team is heading.
-
Marketing and brand strategy; creation and updating of the client management system
We support you in updating your marketing and brand strategy and customer management system, so that you can adapt in this time of rapid changes.
-
Coaching and development support
A good organizational culture is like a trump card for a company. We guide you how to collect trump cards!
-
Digital services
Today, the question is not whether to digitize, but how to do it. We help you develop and implement smart digital solutions.
-
Sales organisation development
Our mission is to improve our customers' business results by choosing the right focuses and providing a clear and systematic path to a solution.
-
Business plan development
A good business plan is a guide and management tool for an entrepreneur, a source of information for financial institutions and potential investors to make financial decisions.
-
Due diligence
We perform due diligence so that investors can get a thorough overview of the company before the planned purchase transaction.
-
Mergers and acquisitions
We provide advice in all aspects of the transaction process.
-
Valuation services
We estimate the company's market value, asset value and other asset groups based on internationally accepted methodology.
-
Forensic expert services
Our experienced, nationally recognized forensic experts provide assessments in the economic and financial field.
-
Business plans and financial forecasts
The lack of planning and control of cash resources is the reason often given for the failure of many businesses. We help you prepare proper forecasts to reduce business risks.
-
Outsourced CFO service
Our CFO service is suitable for companies of all sizes and in all industries. We offer services to our clients in the required amount and competences.
-
Reorganization
Our experienced reorganizers offer ways to overcome the company's economic difficulties and restore liquidity in order to manage sustainably in the future.
-
Restructuring and reorganisation
We offer individual complete solutions for reorganizing the structure of companies.
-
Corporate taxation
We advise on all matters related to corporate taxation.
-
Value added tax and other indirect taxes
We have extensive knowledge in the field of VAT, excise duties and customs, both on the national and international level.
-
International taxation
We advise on foreign tax systems and international tax regulations, including the requirements of cross-border reporting.
-
Transfer pricing
We help plan and document all aspects of a company's transfer pricing strategy.
-
Taxation of transactions
We plan the tax consequences of a company's acquisition, transfer, refinancing, restructuring, and listing of bonds or shares.
-
Taxation of employees in cross-border operations
An employee of an Estonian company abroad and an employee of a foreign company in Estonia - we advise on tax rules.
-
Tax risk audit
We perform a risk audit that helps diagnose and limit tax risks and optimize tax obligations.
-
Representing the client in Tax Board
We prevent tax problems and ensure smooth communication with the Tax and Customs Board.
-
Taxation of private individuals
We advise individuals on personal income taxation issues and, represent the client in communication with the Tax and Customs Board.
-
Pan-Baltic tax system comparison
Our tax specialists have prepared a comparison of the tax systems of the Baltic countries regarding the taxation of companies and individuals.
-
Recruitment services – personnel search
We help fill positions in your company with competent and dedicated employees who help realize the company's strategic goals.
-
Recruitment support services
Support services help to determine whether the candidates match the company's expectations. The most used support services are candidate testing and evaluation.
-
Implementation of human resource management processes
We either assume a full control of the launch of processes related to HR management, or we are a supportive advisory partner for the HR manager.
-
Audit of HR management processes
We map the HR management processes and provide an overview of how to assess the health of the organization from the HR management perspective.
-
HR Documentation and Operating Model Advisory Services work
We support companies in setting up HR documentation and operational processes with a necessary quality.
-
Employee Surveys
We help to carry out goal-oriented and high-quality employee surveys. We analyse the results, make reports, and draw conclusions.
-
HR Management outsourcing
We offer both temporary and permanent/long-term HR manager services to companies.

-
Internal audit
We assist you in performing the internal audit function, performing internal audits and advisory work, evaluating governance, and conducting training.
-
Internal Audit in the Financial Services Sector
We provide internal audit services to financial sector companies. We can support the creation of an internal audit function already when applying for a sectoral activity license.
-
Audit of projects
We conduct audits of projects that have received European Union funds, state aid, foreign aid, or other grants.
-
Prevention of money laundering
We help to prepare a money laundering risk assessment and efficient anti-money laundering procedures, conduct internal audits and training.
-
Risk assessment and risk management
We advise you on conducting a risk assessment and setting up a risk management system.
-
Custom tasks
At the request of the client, we perform audits, inspections and analyzes with a specific purpose and scope.
-
External Quality Assessment of the Internal Audit Activity
We conduct an external evaluation of the quality of the internal audit or provide independent assurance on the self-assessment.
-
Whistleblowing and reporting misconduct
We can help build the whistleblowing system, from implementation, internal repairs and staff training to the creation of a reporting channel and case management.
-
Sustainability advisory
We help solve issues related to the environment, social capital, employees, business model and good management practices.
-
Sustainability audit
Our auditors review and certify sustainability reports in accordance with international standards.
-
Sustainable finance
We help investors to analyze the environmental issues, social responsibility and good management practices of the company of interest.
-
Sustainable tax
Our international tax specialists define the concept of sustainable tax behavior and provide services related to sustainable tax behavior.
-
Digital strategy
We help assess the digital maturity of your organization, create a strategy that matches your needs and capabilities, and develop key metrics.
-
Intelligent automation
We aid you in determining your business’ needs and opportunities, as well as model the business processes to provide the best user experience and efficiency.
-
Business Intelligence
Our team of experienced business analysts will help you get a grip on your data by mapping and structuring all the data available.
-
Cybersecurity
A proactive cyber strategy delivers you peace of mind, allowing you to focus on realising your company’s growth potential.
-
Innovation as a Service
On average, one in four projects fails and one in two needs changes. We help manage the innovation of your company's digital solutions!

The “smart house” concept is becoming the new normal for office buildings, with technology being used to control heating, ventilation, lighting and the opening and closing of doors. But what happens if a cyber criminal manages to gain access to critical systems in the building?
Smart solutions can become a real headache for the owner, if such functions come under the control of a malign influence. An unexpected interruption of service – for example, ventilation and lighting stops working or the power goes out – is a nightmare for any office building, shopping mall or tenant space manager. Besides crippling everyday operations, a cyber attack can also do major damage to reputation. A recent survey conducted by Grant Thornton found that a majority of companies are afraid of precisely the latter consequence of a cyber attack.
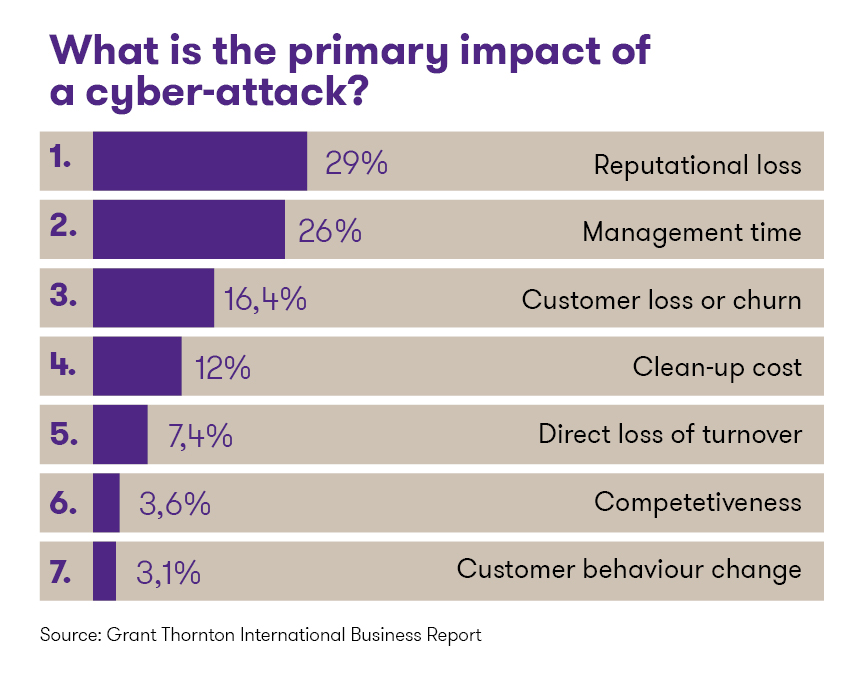
Consequently, dealing with cyber security and data protection must be part of daily operating procedure for the management of companies that run an office building, much like analysis of financial reports. That’s unfortunately not the way it is in real life.
The study also revealed that less than 2/3 of companies (65%) have undertaken activities to map what sorts of data are collected in the company, but they don’t know:
- how much data there is,
- what is done with the data and
- what could happen if the data become compromised.
A report from the State Information System Authority (RIA, see https://www.ria.ee/en/) notes that there were 9,135 cases where cyber security was impacted last year in Estonian computer and data communication networks. Of these, 2,248 – about one-fourth – were found to be cyber security incidents, meaning that the event had a direct impact on the confidentiality, integrity or availability of information or systems. The number of cases this year has grown. The question is no longer if we will be hit by a cyber attack – the question is when.
What are the cyber risks?
According to RIA, the most common cyber risks are malware transmitted by e-mail and spread by web domains, and infected and botnet-controlled devices in communication networks. Phishing and ransomware incidents have received greater public attention – the most recent major case involving the latter was in May, when WannaCry spread around the world. The WannaCry virus encrypted files on infected computers, and criminals demanded a ransom in exchange for the “key”. Considering that WannaCry managed to wreak havoc in 150 countries, including Estonia, it is evident that companies must do more to ensure the security of their information systems.
Cyber criminals look for the “door” of least resistance for breaking into companies and seizing control of data and systems. Sometimes this door is located in the supply chain – for instance, a building’s property management company’s IT system might have weak security, giving the criminals access to a company’s systems located in the building. This can come as a very unpleasant surprise for the building tenants who might have been under the impression that everything is fine in terms of security. Every property management company should thus ask themselves whether they have conducted a thorough IT security analysis and adopted appropriate measures to prevent cyber criminals from accessing their information systems. Every tenant who uses the servers, WiFi network and information systems provided by the lessor company should also ask themselves the same question.
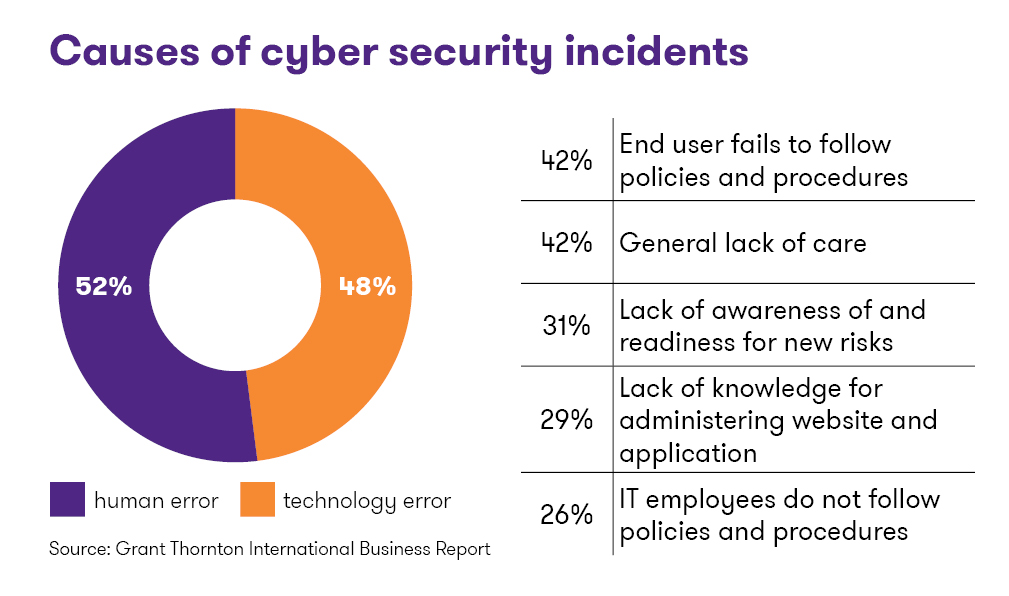
How to increase cyber security?
- Determine your company’s business-critical assets: people, buildings, goods and services, processes, databases. 78% of companies establish data protection procedures without evaluating what their valuable data are.
- Make sure you know what every business-critical asset’s greater vulnerability is, and analyse what types of cyber attacks are most likely in this regard: both now and in the future.
- Control systems should be designed to allow employees, supply chain actors and the public (including website visitors) to access only the information they need.
- Keep the networks for tenants and property management company separate whenever this is appropriate and possible.
- Ensure that there is a good reason for any and all accesses to systems and data.
- Back up important data sufficiently frequently and if necessary, update software.
- Encrypt hard drives, set up a properly configured firewall, use anti-virus protection and, if possible, attack detection systems.
- Do not send critical or sensitive data unencrypted by e-mail. At minimum, use encryption.
- Develop a crisis management plan: who does what first, if you come under cyber attack. Test your crisis management plan regularly!
- Make sure all participants in the supply chain know their duties in ensuring cyber security – every link in the chain is connected to others, too!
- Place special emphasis on raising employee awareness, as people are the weakest link in ensuring cyber security. There will always be someone who, because they don’t know better or weren’t thinking, clicks on a link in an e-mail and infects a computer with malware. Make training employees on IT security topics something your company does on a consistent basis.
Author: Siiri Antsmäe



